According to Gartner, 90% of the organizations that fail to control public cloud use will inappropriately share sensitive data through 2025.
As the public cloud continues to offer more HIPAA-eligible services, those of us at ClearDATA get more and more questions from healthcare organizations about the difference between HIPAA-eligible and HIPAA-compliant services. To help address these questions, we’ve compiled a Q&A on this topic with our Founder and Chief Privacy & Security Officer Chris Bowen.
Can healthcare organizations use any cloud services they want or are they restricted?
There are restrictions when considering public cloud services for sensitive healthcare data. Key regulatory frameworks govern the use of Protected Health Information (PHI) and Personally Identifiable Information (PII), regardless of whether that data is being used on-premise or on the cloud. HIPAA is the most famous. Bear in mind, HIPAA was written over 20 years ago and was not prescriptive in its language even then, but now can be increasingly hard for organizations to interpret in light of the new technologies that have come into play. But the work behind what HIPAA enforces is critically important. The safety and privacy of patient data must be protected. There are other frameworks as well, such as the fairly recently implemented General Data Protection Regulation (GDPR). When a healthcare or life sciences organization wants to move to the cloud and use native cloud services, it can only use services that are deemed HIPAA-eligible for any workloads that contain PHI.
What are my options for HIPAA cloud compliance?
The three main public clouds, Amazon Web Services, Microsoft Azure, and Google Cloud Platform, serve a variety of industries. It’s important to remember that healthcare is a highly regulated industry, and it is not the primary or sole focus of these three public clouds the way it is for ClearDATA, since we are healthcare-exclusive. As part of these clouds’ day-to-day operations, they are constantly evolving cloud services; in fact, sometimes they add hundreds of updates and new services every month. What matters to healthcare organizations as more and more move to the cloud, is understanding which of these services can be configured appropriately to store, transmit, or process protected health information (PHI) and personally identifiable information (PII).
So, if a service is HIPAA eligible it’s okay to use with PHI, right?
That’s where it gets a little complicated. The answer is yes, and no. Think of it this way. I can go to the store and get a bunch of ingredients to create a delicious Italian dinner like the one I recently had at a trending restaurant. My ingredients might be chicken cacciatore eligible in that they are what is needed to create that dish. But I may not know how to use and assemble them to get to that result. I may not know which technical controls to configure, or how. The same is true for cloud services.
A service that is HIPAA eligible is one that is capable of being configured in a way that could meet HIPAA compliance requirements, but you have to know how to do it, it doesn’t happen ‘out of the box.’
And it’s not just configuring it properly at deployment – you have to know how to keep it compliant for the lifetime of your application because data is not stagnant and is likely to drift in and out of compliance. So a service may be HIPAA-eligible, but it is on the customer (or a partner they hire to help with this) to make it HIPAA compliant, which most healthcare organizations struggle with as it’s not their area of expertise… just like you can give me a kitchen counter full of food that could make chicken cacciatore, but it might not end up being that once I assemble it.
What goes into making a HIPAA-eligible service into a HIPAA-compliant one?
You need a deep knowledge of healthcare regulations, as well as extensive cloud expertise, and the dedication and focus to stay in front of the wave of innovation by the three major cloud providers for the life of your application. The three have to be orchestrated together. You must be able to map and enable or disable technical controls available in the cloud to the various regulations to meet the criteria necessary to maintain compliance in your infrastructure.
What are HIPAA technical controls?
Here is a chart with examples of some technical controls. If you read through you can see what they can control. These services are not built exclusively for healthcare – they are built to be able to store, transmit, or process data, whether for banking, retail, finance, government, or healthcare. That doesn’t mean it’s doing it in a way that meets the complex regulatory requirements of healthcare right ‘out of the box.’
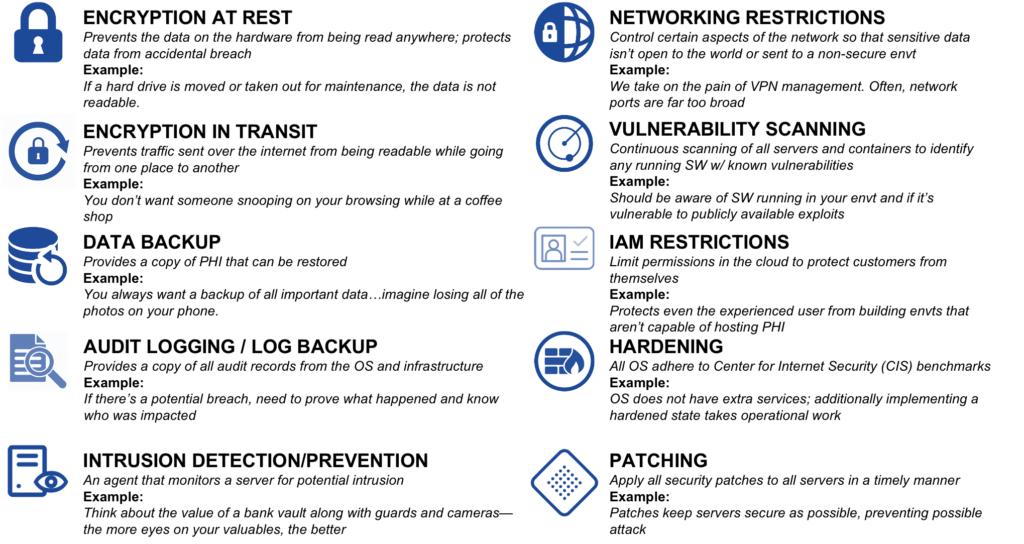
How does a healthcare organization know which technical control should be used to map to which regulation be it HIPAA, NIST, or others?
That’s where the many customers who have come to us have previously struggled. The regulations don’t tell you. Because ClearDATA is a cloud expert and healthcare exclusive with HITRUST certification, we’ve spent nearly the last decade staying on top of this. Our CyberHealth™ Platform gives stakeholders a constant view into which controls for each service map to the regulations as well as how we interpret the regulation to be sure the adequate level of privacy and security are being adhered to to maintain compliance. Here’s an example of how that can get complex for people who don’t do this full-time, with examples from both HIPAA and GDPR:
- HIPAA 45 CFR 164.312(e)(1): Implement technical security measures to guard against unauthorized access to PHI that is being transmitted over an electronic communications network.
- GDPR, Article 32, Section 1(a): Security of Processing – Taking into account the state of the art, the costs of implementation and the nature, scope, context, and purposes of processing as well as the risk of varying likelihood and severity for the rights and freedoms of natural persons, the controller and the processor shall implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk, including inter alia as appropriate: The pseudonymization and encryption of personal data.
So, what do these really mean? They mean data (PHI or PII) in transit must be secured—but the regulations don’t specify how. The most broadly accepted control today is to encrypt the data using Transport Layer Security (TLS). To do that, the organization would need to determine which cloud services their team is using have the TLS option for configuration. Then the organization has to figure out how to enforce that for the application data flows.
How can I architect cloud-based applications with the CyberHealth Platform?
As a HITRUST-certified organization, we understand the importance of protecting sensitive healthcare data and the risks and consequences that occur if the proper precautions are not put in place. Exclusive to healthcare and life sciences, we help hundreds of organizations harness healthcare data in the public cloud in a secure and compliant manner. As a result, these organizations can use the cloud to build innovative applications, whether transforming a member portal, building software as a medical device, or using the cloud to uncover insights from a clinical trial faster. We don’t just understand HIPAA—we have expertise around numerous standards such as GDPR, GxP, NIST, and HITRUST.
Our expert interpretation of the regulations and deep knowledge of cloud services is the foundation of our platform, which enforces the relevant technical controls to keep PHI secure throughout the lifecycle of our customers’ applications.
How does this software, the CyberHealth Platform, work?
The CyberHealth Platform is a cloud security posture management (CSPM) solution that helps healthcare organizations monitor and manage their privacy and compliance obligations in the public clouds: AWS, Azure, and Google Cloud.
Our mapping and opinionated stance are visible in the software, giving you a resource for auditors as well as documentation for your team. We have automated the controls, or safeguards to help maintain your compliance stature and set up alerts and remediation if you drift out of compliance.


