Managed Detection & Response (MDR)
Healthcare threats? Not in your cloud ecosystem.

Shield PHI as cloud threats evolve.
Minimize looming healthcare threats by decreasing your cloud attack surface and mitigating vulnerabilities.
Defend against attacks.
Access our exclusive healthcare intelligence network, get advanced threat detection and vulnerability protection, and neutralize threats five times faster with ClearDATA than on your own.
Minimize cloud risk.
Choose from tailored security operations (SecOps) solutions built for healthcare, see priotized threats clearly, and close cloud exposure with expert guided and automated remediation.
Lean on the experts.
Count on our team’s combined decades of cybersecurity and compliance expertise, delivering unparalleled protection tailored to the intricacies of healthcare compliance–without breaking the bank.
Healthcare’s cybercriminals don’t clock out.
Neither do we.Purpose-built for healthcare, Managed Detection & Response (MDR) proactively detects, investigates, and neutralizes cyber risks.
With continuous threat monitoring, automated safeguards, and expert-led incident response, we reduce your cloud attack surface and keep sensitive data secure.
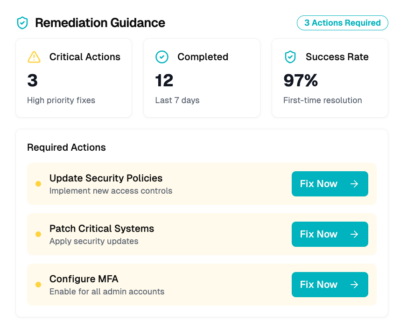
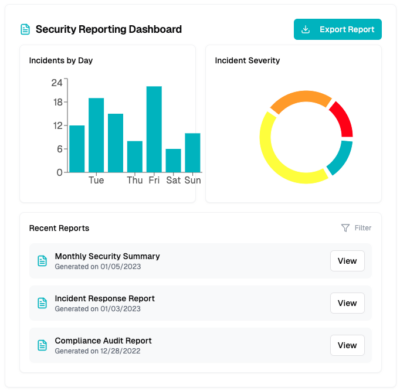
Clearly see prioritized security incidents, risk levels, and remediation progress to protect your cloud’s healthcare data.
Detection & Response Features
XDR tuning
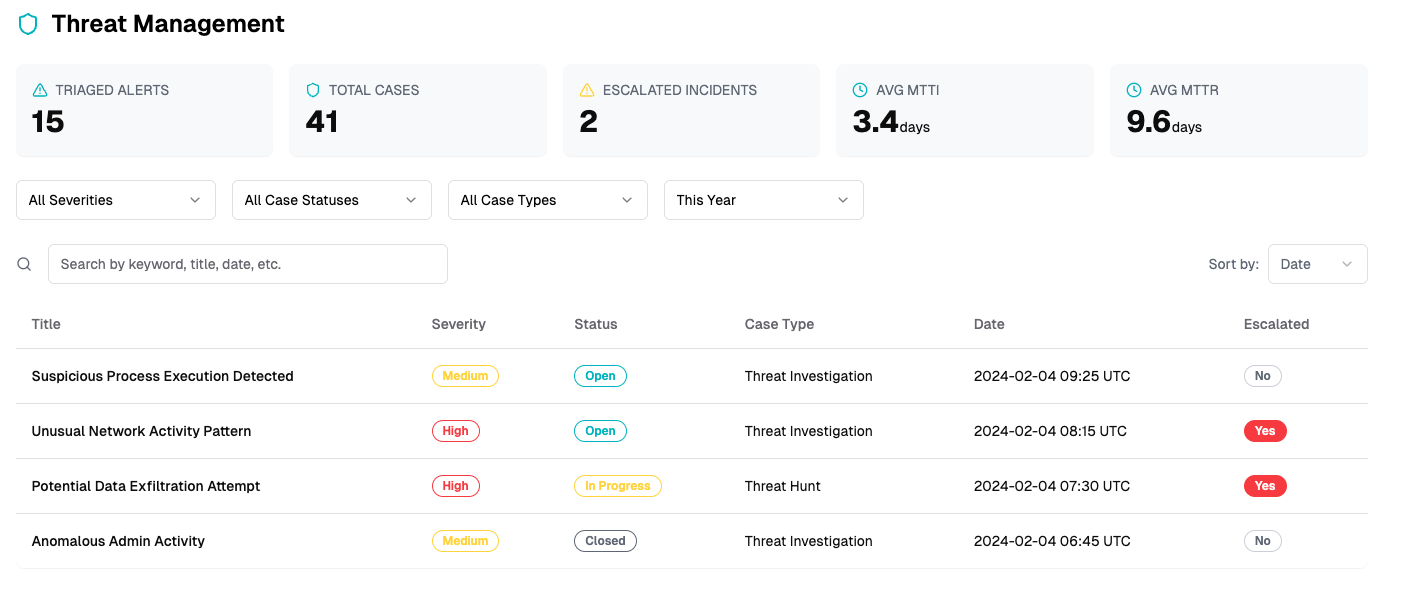
Detect and analyze
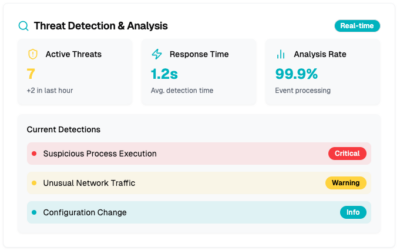
Threat hunting, detection, and investigation
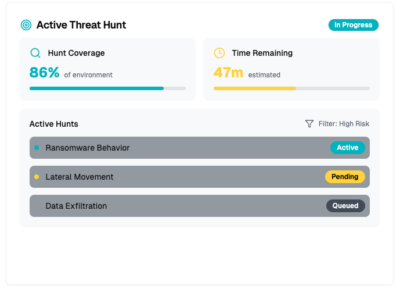
Analyst-initiated threat response
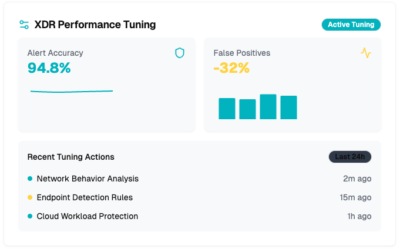
XDR Tuning
Tailor Extended Detection & Response (XDR) capabilities to meet the specific needs of your environment, enhancing threat detection precision.
Insights, Analysis, Guidance & Reporting Features
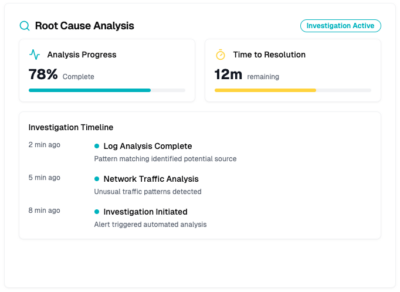
Root cause analysis and RFIs
Remediation guidance
Reporting
Root Cause Analysis and Requests for Intelligence (RFI)
Gain valuable insights through in-depth root cause analysis and tailored intelligence requests, helping prevent future incidents.
Choose Your Level of Protection
MDR Service Tiers
As the sole healthcare-specific managed service provider alongside you on your cloud journey, we can help you transition cybersecurity from headache to strategic advantage. Choose your tailored level of security protection from our two service tiers.
MDR Essentials
Essential security monitoring and threat hunting with incident escalation
- Threat detection and response with a core set of XDR features
- Proactive threat hunting and alert management (triage, investigation, notification)
- Potential security incidents are escalated to your internal team for resolution
MDR Complete
End-to-end protection with advanced containment and recovery assistance
- Builds on all services included in MDR Essentials
- Comprehensive XDR features for protecting entire public cloud environments
- Analyst-initiated threat containment
- Expert guidance for eradication and incident recovery
Technology Integration: Core Managed Extended Detection & Response (XDR)
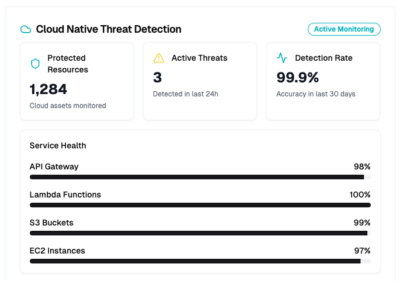
Cloud native threat detection service monitoring
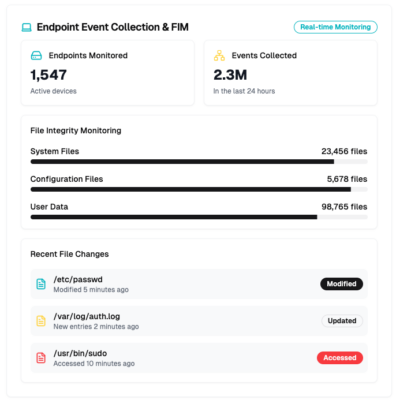
Endpoint extended event collection and FIM
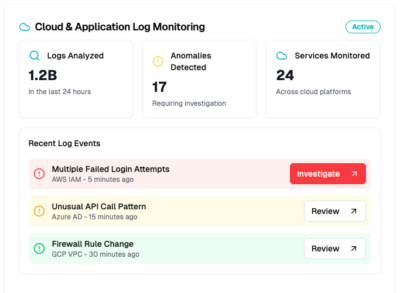
Cloud and common application log monitoring
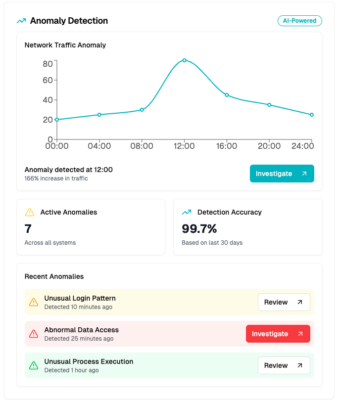
Anomaly detection
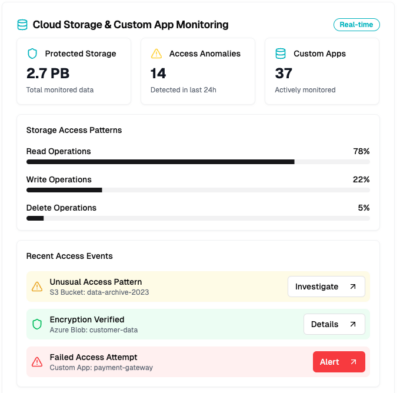
Cloud storage access and custom application log monitoring
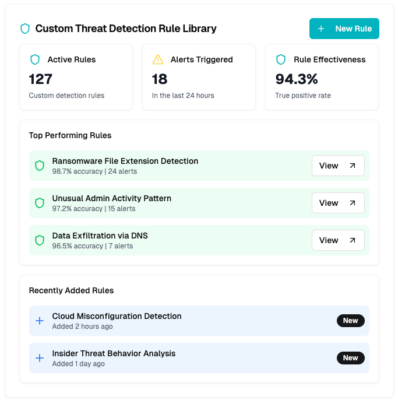
Custom threat detection rule library
Cloud Native Threat Detection Service Monitoring
Observing and analyzing services within your cloud environment to identify potential threats and vulnerabilities inherent to cloud-native applications.
Credentialed. Celebrated. Certified.