Healthcare data visualization and insights
Get the full picture with the
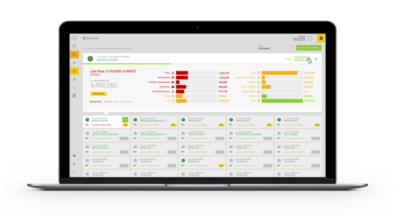
CyberHealth™ platform
Our privacy and security management tooling lets you identify, visualize and strategically prioritize risk to protect PHI data across all cloud environments through a single pane of glass, with full protection from our Endpoint Security software, Elastic Defend.
Identity Access Management visualization
Sensitive data discovery and inventory
Endpoint security and protection
Address access and permissions
Identity Access Management visualization
Visualize IAM clearly through a security lens to manage and understand the scope of risk. Gain immediate insight into:
- Individuals and roles with access to specific resources, which resources give permissions to whom, and which applications have access to those resources
- Stale resources
- Least privilege enforcement
- PHI containing resources
- Individuals granted access to PHI

Leverage our platform and services to locate and protect your sensitive data so you can safely accelerate your innovation in the cloud.
Speak with a
expert today
Credentialed. Celebrated. Certified.