Data Liquidity Increases with User Access and Third Parties
Healthcare organizations face a complex web of third-party organizations and systems, each with their own overlapping identity and access control options. These connected systems produce permissions sprawl, creating risks and introducing vulnerabilities. For instance, insiders abusing privileged access continue to be one of the main causes of data leaks, attributing to 39% of healthcare data breaches in 2020.
How Can Healthcare Combat Permission Sprawl?
User access must be monitored and controlled. Identity and Access Management (IAM) systems are used to centralize administration of access rights, but they have significant limitations. It is normally cumbersome to understand what set of assets a given user has access to, let alone how their access compares to their peers. IAM products are focused on the granting and removing of permissions, not providing good visualizations of how those permissions connect with each other.
ClearDATA Helps Healthcare with IAM Visualization
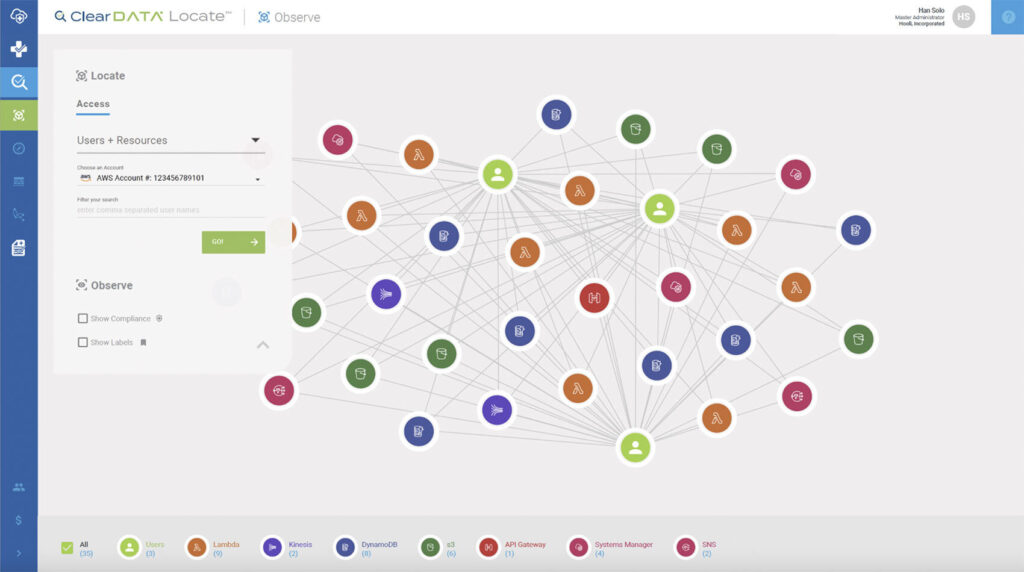
ClearDATA’s IAM Visualization capability fills that gap in IAM products. With ClearDATA, you can gain a comprehensive view of your IAM, including who has what permissions and what systems those permissions give them access to. This new level of visualization can help you manage and understand risks associated with permissions by gaining insight into:
- The individuals and roles with access to resources, what other resources they can also connect to, and which applications have access to those resources.
- Which users have permissions that differ from their peers and what additional access rights they have.
- Which permission(s) give users access to a given resource, which other permissions allow access to the same resource, and who has those other permissions.
- Least privilege enforcement.
- Do users and roles have large amounts of permissions that aren’t being used?
- Do we have stale sensitive data?
- Do I have sensitive data that isn’t being used and would be better off deleted?
- PHI-containing resources, which individuals have access to those resources, and how were they given that access?
This type of technology can help you avoid a breach like Montefiore experienced when an insider accessed sensitive data, including health records and clinical information such as lab results and patient diagnoses. Contact us to learn more about how ClearDATA is arming healthcare to combat permission sprawl with IAM visualization.


