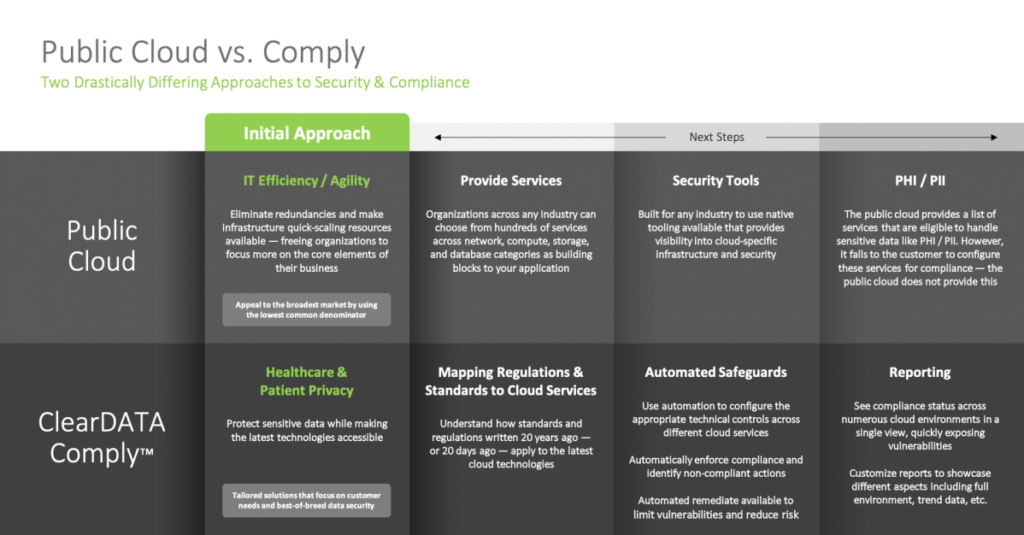
The public cloud provides building blocks for organizations to build and develop quickly, in an agile manner. Most people immediately think of database and storage as capabilities available as services via the cloud; however, AWS, Azure, and Google Cloud also provide their own security tools to help organizations secure their infrastructure.
Bear in mind, all three public clouds serve a wide variety of verticals—they are not focused exclusively for healthcare, and are therefore not building exclusively for healthcare.
Each public cloud provides their own set of tools, built by that cloud, for that cloud, which provides advantages from a seamless integration standpoint—but that also means each cloud’s approach is a bit different. Below is a breakdown of how AWS, Azure, and GCP approach security tooling:
- AWS Approach: AWS has built a suite of tools that allow customers to protect their data, protect their infrastructure, respond to incidents, and monitor it all through the AWS Security Hub. Additionally, customers can extend their security through access to the world’s largest ecosystem of security partners and solutions through the AWS Partner Network and the AWS Marketplace.
- Azure Approach: Microsoft has built a world-class comprehensive security suite that automatically monitors Azure resources including VMs and other services and with built-in security controls within the hardware and firmware. Azure Security Center sits at the nexus of Azure environments providing a unified infrastructure security management system that provides both visibility and advanced threat detection for your Azure cloud workloads.
- GCP Approach: Google has been integrating many security features into the Cloud Security and Command Center (CSCC) at the Organization level which also includes the ability for customers to build their own compliance policy to monitor. This is a centralized place where all potential security and compliance events are surfaced for GCP.
The public clouds have invested significant resources into integrating security into their offering so that organizations across the world and across a variety of industries can leverage the benefits cloud has to offer.
For more regulated industries like healthcare, the public cloud security tooling isn’t enough to address the ambiguous compliance regulations to which healthcare and life sciences organizations must adhere.
The difference between compliance and security is often a source of confusion. Resources can be secure but not compliant and the reverse can exist, too. On top of that, there are typically two different organizations: one focused on compliance and then another organization completely dedicated to security. The end goal, of course, is putting in place strong security and compliance strategies to reduce risk for the organization. That’s where ClearDATA can help.
ClearDATA Comply™ software was created to help healthcare organizations manage privacy, security and compliance in the cloud. ClearDATA is a HITRUST-certified organization exclusively serving the healthcare and life sciences industries. We approach our product development through a healthcare business lens, assuring the critical standards, regulations, and frameworks our customers must follow such as HIPAA and GDPR are addressed to the highest standard.
Comply software contains a robust set of technical controls that enforce automated and ongoing compliance for cloud environments. Comply, by design, uses many of the cloud native tools to know when new resources are created or when there are changes made across the environment that may impact compliance. While the value of Comply lies in the entire process from raw telemetry detection through evaluation, remediation, and finally compliance reporting, the tools provided by our cloud partners are valuable and serve as a solid base.
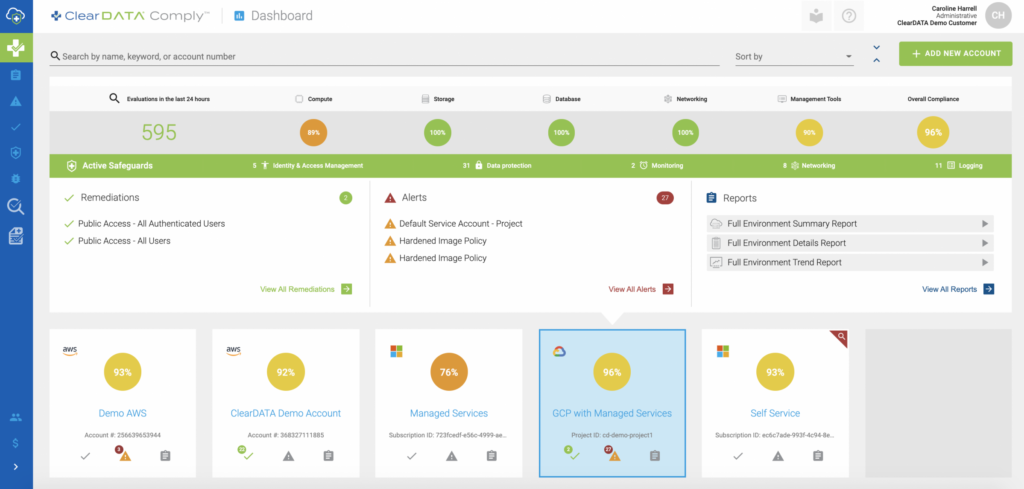
ClearDATA Comply provides a multi-cloud view of the compliance status of your environments.
Cloud native security tools provide a deeper view into the cloud infrastructure with an operational lens, and even a security lens; however, they typically do not provide the last connection point of mapping to technical controls that is critical to healthcare.
For example, Amazon CloudWatch can monitor if a server is down and Amazon Systems Manager can provide information about patching baselines for EC2 instances, resulting in compliance data being located across many services, as well as operational data that has no impact to your compliance posture. With a healthcare-first approach instead of IT or app-first approach, Comply elevates and demonstrates compliance and security information to customers via robust reporting and near real-time dashboards. Read on to learn how native tooling from each of the public clouds benefits from the additional layer of protection provided by Comply:
AWS:
- Comply ingests telemetry from AWS Config, CloudTrail, and CloudWatch to perform evaluations and remediations based on the crucial events that occur within an AWS environment.
- Comply uses these events to ensure the ongoing compliance of the cloud environment by using automation to remediate non-compliant services and alerting the customer of the remediation.
- Comply provides reports informing customers of their current compliance status, as well as their compliance trends over time.
- Comply maps the evaluations to healthcare-specific requirements that healthcare organizations must follow to remain compliant.
Azure:
- Comply relies on tooling and features in Azure Security Center to perform certain functions, such as Advanced Threat Detection for Azure SQL.
- Comply also uses Azure Policy to evaluate and enforce Automated Safeguards.
- Whereas Azure Security Center can provide both a current security and compliance view for some frameworks for your environment, such results are ephemeral unless additional steps are taken to preserve data and build reporting on it. Comply builds on top of Azure Security Center to provide rich reporting both for near real-time and historical compliance status. Comply will also proactively ensure certain controls for compliance, such as enabling logging, are satisfied through remediation.
- Furthermore, Security Center provides a broad set of recommendations, many of which are not applicable to healthcare, and some may need additional evaluation to best fit your environment. Comply provides focus on the data coming from Security Center and other Azure features, showing the data that is important to our healthcare customers.
- While regulatory compliance is an enhanced feature available to Azure Security Center, the primary alignment is from technology to control but it does not include information mapping to the specific HIPAA CFR.
Google Cloud Platform:
- The tool is still early in its lifecycle and has a very textual/grid-based interface. Finding events that are important for you out of the numerous events surfaced can be cumbersome.
- The CSCC offers to remediate a few controls, like public cloud storage bucket, that is triggered inside the CSCC console, but it is not automated.
- The CSCC can consume events detected by Forseti, Google’s open source compliance tool for GCP. This is the same tool that ClearDATA built for Comply (see blog post to learn more about our work with Forseti) to consume compliance events and automatically remediate compliance violations in our customer projects. Installing Forseti, developing policy, updating Forseti policy when new GCP features and services are released and maintaining Forseti is a large undertaking. ClearDATA Comply manages all of this for you.
Each cloud’s security tooling described above is native to that cloud, which is great when you’re only working with one cloud provider; however, the growing trend of cloud strategy diversification to multi-cloud makes getting a holistic view of an entire organization’s cloud compliance more than challenging.
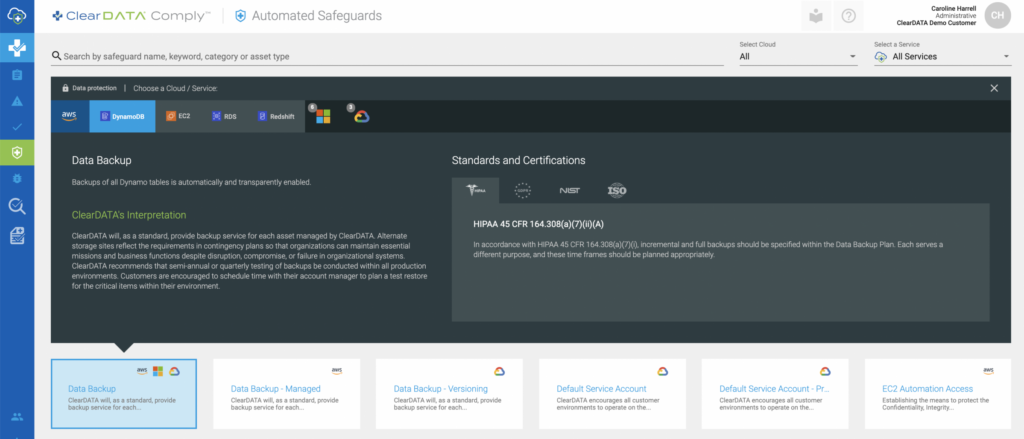
Comply provides a single pane view of your compliance status across different clouds and different accounts, supported by a common prescriptive interpretation within the software.
It’s also important to keep in mind that cloud native “HIPAA Eligible” services are not necessarily configured to be HIPAA compliant out of the box. The cloud vendors offer these HIPAA Eligible services that are HIPAA Eligible or BAA Covered, which means they can be used to host or process PHI if they are configured to meet those requirements. The answer to the question “What goes into making a HIPAA-eligible service HIPAA compliant?” is a very important one. The answer:
Organizations need:
1. Deep knowledge of healthcare regulations
2. Extensive cloud expertise
3. Dedication and focus to stay in front of the waves of constant innovation by the three public cloud providers throughout the lifecycle of your application
These 3 areas of expertise must be orchestrated together rather than siloed throughout different teams and organizations in order to use services that are eligible to handle PHI/PII in a compliant manner. Organizations need to map and enable or disable technical controls available in the cloud to the various regulations in order to meet the criteria necessary to maintain compliance in your infrastructure. To learn more, read the article.
While Comply and cloud native tools may have some overlap in certain controls and certain use cases, only Comply has the healthcare focus that unifies three clouds and helps our customers maintain compliance for their cloud environments.


